OpenStack の概要¶
本ガイドは、OpenStack のデプロイメントにおけるセキュリティに関する知見を提供します。クラウドアーキテクト、デプロイ担当者、管理者などを対象読者としています。また、クラウドユーザーには、プロバイダー選択にあたって参照することのできる有用な情報を記載している一方、監査担当者には、コンプライアンス認証に伴う作業を支援する参考資料としてご利用いただくことができます。本ガイドは、クラウドのセキュリティに関心を持つ読者全般にもお奨めします。
Each OpenStack deployment embraces a wide variety of technologies, spanning Linux distributions, database systems, messaging queues, OpenStack components themselves, access control policies, logging services, security monitoring tools, and much more. It should come as no surprise that the security issues involved are equally diverse, and their in-depth analysis would require several guides. We strive to find a balance, providing enough context to understand OpenStack security issues and their handling, and provide external references for further information. The guide could be read from start to finish or used like a reference.
We briefly introduce the kinds of clouds (private, public, and hybrid) before presenting an overview of the OpenStack components and their related security concerns in the remainder of the chapter.
Throughout the book, we refer to several types of OpenStack cloud users: administrator, operator, and user. We use these terms to identify the level of security access each role has, although, in reality, we understand that varying roles are often held by the same individual.
クラウドのタイプ¶
OpenStack is a key enabler in the adoption of cloud technology and has several common deployment use cases. These are commonly known as Public, Private, and Hybrid models. The following sections use the National Institute of Standards and Technology (NIST) definition of cloud to introduce these different types of cloud as they apply to OpenStack.
パブリッククラウド¶
According to NIST, a public cloud is one in which the infrastructure is open to the general public for consumption. OpenStack public clouds are typically run by a service provider and can be consumed by individuals, corporations, or any paying customer. A public-cloud provider might expose a full set of features such as software-defined networking or block storage, in addition to multiple instance types.
By their nature, public clouds are exposed to a higher degree of risk. As a consumer of a public cloud, you should validate that your selected provider has the necessary certifications, attestations, and other regulatory considerations. As a public cloud provider, depending on your target customers, you might be subject to one or more regulations. Additionally, even if not required to meet regulatory requirements, a provider should ensure tenant isolation as well as protecting management infrastructure from external attacks.
プライベートクラウド¶
At the opposite end of the spectrum is the private cloud. As NIST defines it, a private cloud is provisioned for exclusive use by a single organization comprising multiple consumers, such as business units. The cloud may be owned, managed, and operated by the organization, a third-party, or some combination of them, and it may exist on or off premises. Private-cloud use cases are diverse and, as such, their individual security concerns vary.
コミュニティクラウド¶
NIST defines a community cloud as one whose infrastructure is provisioned for the exclusive use by a specific community of consumers from organizations that have shared concerns (for example, mission, security requirements, policy, or compliance considerations). The cloud might be owned, managed, and operated by one or more of organizations in the community, a third-party, or some combination of them, and it may exist on or off premises.
ハイブリッドクラウド¶
A hybrid cloud is defined by NIST as a composition of two or more distinct cloud infrastructures, such as private, community, or public, that remain unique entities, but are bound together by standardized or proprietary technology that enables data and application portability, such as cloud bursting for load balancing between clouds. For example, an online retailer might present their advertising and catalogue on a public cloud that allows for elastic provisioning. This would enable them to handle seasonal loads in a flexible, cost-effective fashion. Once a customer begins to process their order, they are transferred to a more secure private cloud that is PCI compliant.
In this document, we treat community and hybrid similarly, dealing explicitly only with the extremes of public and private clouds from a security perspective. Your security measures depend where your deployment falls upon the private public continuum.
OpenStack サービスの概観¶
OpenStack は、モジュール型アーキテクチャを採用し、中核的な設計理念としてスケーラビリティと柔軟性を促進する一式のコアサービスを提供します。本章では、OpenStack のコンポーネントとそれらのユースケースおよびセキュリティに関する考慮事項を簡単に説明します。
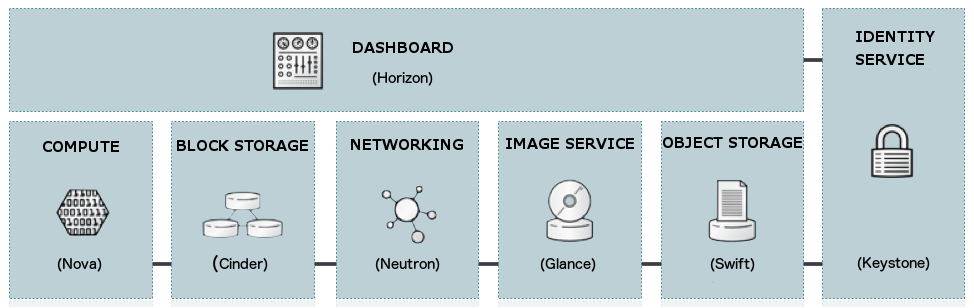
Compute¶
OpenStack Compute service (nova) provides services to support the management of virtual machine instances at scale, instances that host multi-tiered applications, dev or test environments, "Big Data" crunching Hadoop clusters, or high-performance computing.
The Compute service facilitates this management through an abstraction layer that interfaces with supported hypervisors (we address this later on in more detail).
本ガイドの後半では、ハイパーバイザーと関連する仮想化スタックに焦点をあてて、包括的に解説します。
For information about the current state of feature support, see OpenStack Hypervisor Support Matrix.
Compute security is critical for an OpenStack deployment. Hardening techniques should include support for strong instance isolation, secure communication between Compute sub-components, and resiliency of public-facing API endpoints.
Object Storage¶
The OpenStack Object Storage service (swift) provides support for storing and retrieving arbitrary data in the cloud. The Object Storage service provides both a native API and an Amazon Web Services S3-compatible API. The service provides a high degree of resiliency through data replication and can handle petabytes of data.
It is important to understand that object storage differs from traditional file system storage. Object storage is best used for static data such as media files (MP3s, images, or videos), virtual machine images, and backup files.
Object security should focus on access control and encryption of data in transit and at rest. Other concerns might relate to system abuse, illegal or malicious content storage, and cross-authentication attack vectors.
Block Storage¶
The OpenStack Block Storage service (cinder) provides persistent block storage for compute instances. The Block Storage service is responsible for managing the life-cycle of block devices, from the creation and attachment of volumes to instances, to their release.
Block Storage のセキュリティ課題は、Object Storage の場合と同様です。
ネットワーク¶
The OpenStack Networking service (neutron, previously called quantum) provides various networking services to cloud users (tenants) such as IP address management, DNS, DHCP, load balancing, and security groups (network access rules, like firewall policies). This service provides a framework for software defined networking (SDN) that allows for pluggable integration with various networking solutions.
OpenStack Networking allows cloud tenants to manage their guest network configurations. Security concerns with the networking service include network traffic isolation, availability, integrity, and confidentiality.
Dashboard¶
The OpenStack Dashboard (horizon) provides a web-based interface for both cloud administrators and cloud tenants. Using this interface, administrators and tenants can provision, manage, and monitor cloud resources. The dashboard is commonly deployed in a public-facing manner with all the usual security concerns of public web portals.
Identity¶
The OpenStack Identity service (keystone) is a shared service that provides authentication and authorization services throughout the entire cloud infrastructure. The Identity service has pluggable support for multiple forms of authentication.
Security concerns with the Identity service include trust in authentication, the management of authorization tokens, and secure communication.
Image サービス¶
The OpenStack Image service (glance) provides disk-image management services, including image discovery, registration, and delivery services to the Compute service, as needed.
前述したデータセキュリティに関する問題と同様に、ディスクイメージのライフサイクル管理には信頼されたプロセスが必要です。
その他の支援技術¶
Messaging is used for internal communication between several OpenStack services. By default, OpenStack uses message queues based on the AMQP. Like most OpenStack services, AMQP supports pluggable components. Today the implementation back end could be RabbitMQ, Qpid, or ZeroMQ.
Because most management commands flow through the message queuing system, message-queue security is a primary security concern for any OpenStack deployment, and is discussed in detail later in this guide.
Several of the components use databases though it is not explicitly called out. Securing database access is yet another security concern, and consequently discussed in more detail later in this guide.
